Networked control systems
This research project is not currently active and this page is not regularly updated. It is provided here for archival purposes.

Networked control systems consist of many spatially distributed sensors, actuators, and processors that can communicate with one another over a wired or wireless computer network. Rapid advances in sensing technologies are revealing unprecedented dynamic data streams about diverse physical, technological, and social network dynamics, and new actuation technologies are increasing the ability to manipulate network architecture and dynamics. Traditional methods from control theory are not suitable for analyzing and designing such networks due to computational complexity and inability to deal with constraints imposed by the network such as structural information flow constraints, data loss and corruption, bandwidth limits, and variable delays. Research in this area brings together results from control, optimization, information and communication theory, computer science, data mining and statistics, and others to form a theoretical foundation.
Major advancements over the last decades in wired and wireless communication networks gave rise to the new paradigm of Networked Control Systems (NCS). Within this paradigm, sensing and actuation signals are exchanged among various parts of a single system or among many subsystems via communication networks; the latter scenario is seen in Fig. 1.
Although this enables one to perform more complex tasks than traditional control paradigms, it comes at the cost of complicating the design phase and the required analysis tools. For example, the communication networks may introduce time-varying time delays, imperfect information exchange, information loss, etc. This affects the performance of any control laws that were designed without taking the network effects into account. Therefore, it becomes of paramount importance to address some of the following theoretical problems:
- Characterizing stability conditions for NCS.
- Minimizing the amount of information exchange within the overall system.
- Robustifying the system with respect to the network effects at the design phase.
One aim of this group is to look at the theoretical issues mentioned above and adapt some of these concepts to two relevant applications:
Further research explores cyber-physical security for critical infrastructures.
- Security of cyber-physical systems & critical infrastructures
Area surveillance using multiple cameras
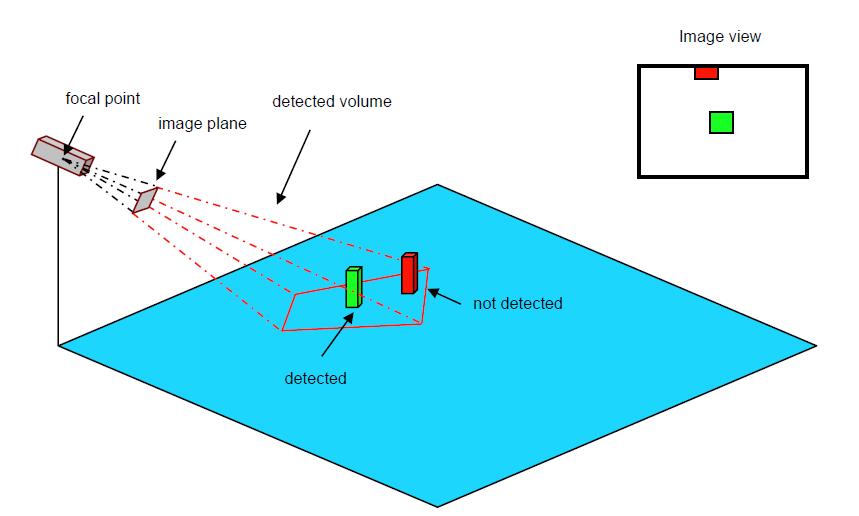
We study the problem of surveillance and multi-target tracking using multiple cameras. The cameras are of Pan-Tilt (PT) or Pan-Tilt-Zoom (PTZ) and they are mounted at given locations in the environment. The problem is to design an optimization-based controller that is predictive in nature, in the sense that it takes into account the possible future motion of the targets in the optimization problem. The areas of coverage of the cameras may overlap, and as such it becomes necessary to hand off targets from one camera to another in some optimal or suboptimal fashion. We consider the 3 dimensional (3D) geometry of the problem and take into account the nonlinearities that result from the rotation between reference frames as well as the projection onto the image view of the cameras. The underlying optimization problem takes into account the effects of the geometry, the actuation constraints of the cameras, and the maximal possible speed of the targets being tracked. We are also considering hand-offs among the cameras as a scheduling problem over the optimization horizon. The local controller for each camera implements the tracking of multiple targets via a priority-based optimization problem. The resulting optimization problem is naturally a mixed-integer program, which can be implemented in Matlab. An illustration of the geometric aspects of this problem for a single camera and two targets is show in Fig. 1 below.
Cyber attacks in power networks
In large-scale electric power systems, IT infrastructures that provide system-wide supervision and control set-points have been already developed. These systems, known as Supervisory Control and Data Acquisition (SCADA) systems, collect data from remote facilities and send back control commands to the power system. The dependence of power systems on this infrastructure makes them susceptible not only to operational errors but also to external cyber attacks. Our goals are to
- investigate the impact of such cyber attacks on a large 40-bus network monitored by a SCADA system,
- determine the vulnerabilities of the interconnected cyber-physical model, and
- specify the possible attack paths and construct efficient mitigation strategies so as to restore the system and/or avoid cascading failures
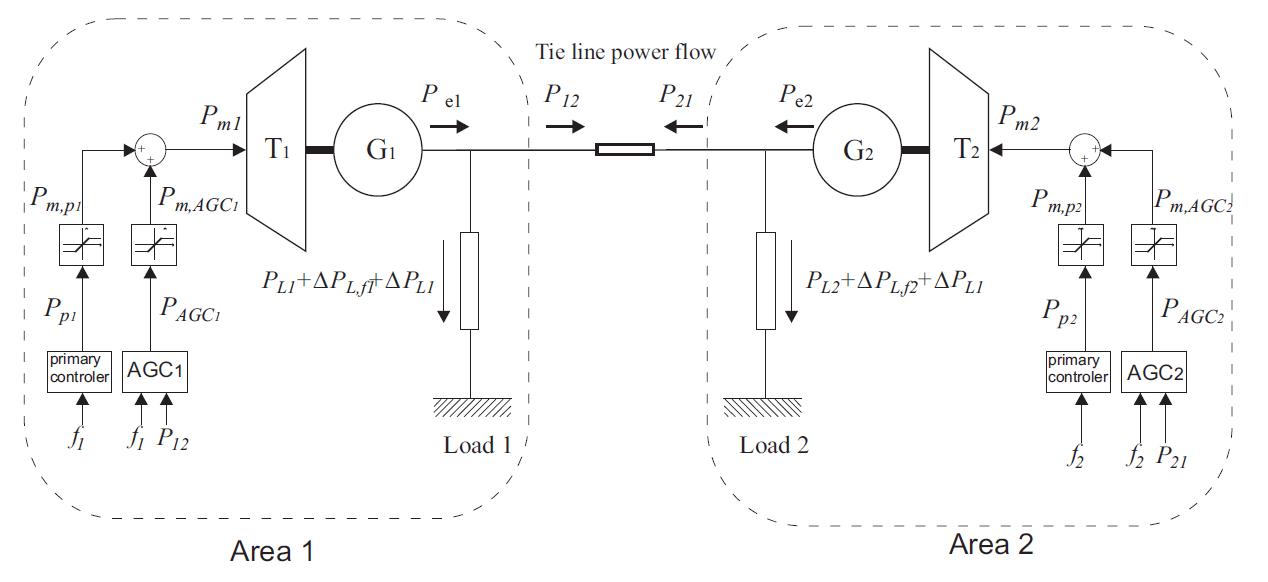
As a first step, we studied the safety of a lumped two-area power system (Fig. 2), and developed a methodology to identify and evaluate the impact that a cyber attack on the Automatic Generation Control (AGC) might have. The primary objective of the AGC, which is one of the few control loops that are closed over the SCADA system without human operator intervention, is to regulate the frequency of each area to the nominal value and maintain the power exchange between the networked two-areas system at a specified level.
We study the impact that such an attack could have by using reachability methods. This way we can detect if a potential attacker is able to construct a policy so as to irreversibly disturb the system. As such, we are interested in providing answers to the following problems:
- Is the attacker able to steer at least one of the frequencies of the two areas outside of a given safe region?
- Could the power exchange limits between the two areas be violated?
- What is the smallest bound for the input of the attacker so as to achieve his goal, i.e. disturb the system?
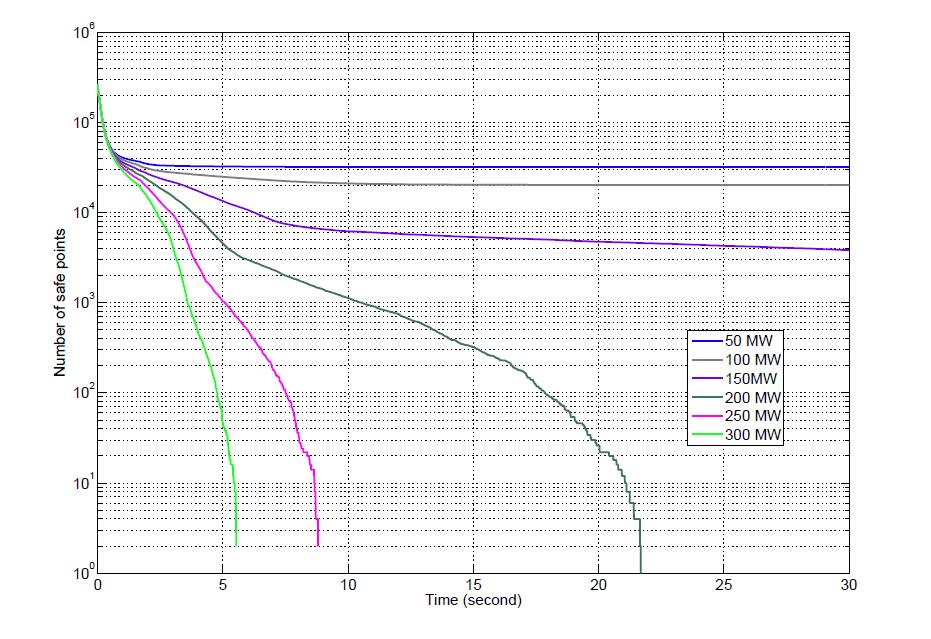
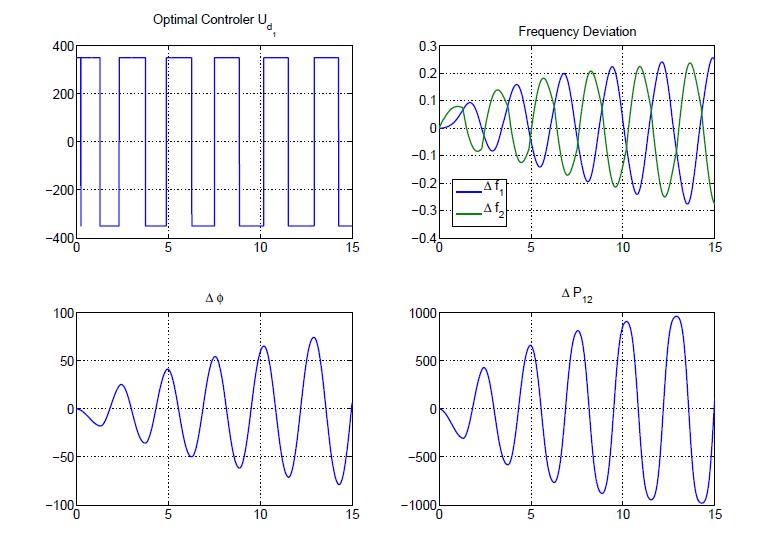
Fig. 3 shows a family of curves that correspond to different bounds of the attack signal. Based on this data, ±200 MW is the minimum signal that an attacker could use in order to disturb the system. Although the frequency bounds in this simple system can not be violated, the attacker is able to construct a policy so as to violate the power exchange limits between the two areas infinitely often, and hence lead to power swinging (Fig. 4).
Security of Cyber-Physical Systems & Critical Infrastructures
Cyber-physical systems are ubiquitous in industrial automation systems and critical infrastructures, such as power generation, water and gas distribution, as well as transportation networks. The integration of cyber technologies with physical processes increases system efficiency but, at the same time, it introduces vulnerabilities that undermine the reliability of critical infrastructures. Some infamous examples include the StuxNet computer worm, the Maroochy water breach, and the SQL Slammer worm attack on the Davis-Besse nuclear plant. Thus, cyber-physical systems need to operate reliably in face of unforeseen failures and external malicious attacks. In our external page work, we propose a mathematical framework for cyber-physical systems, malicious attackers, and security monitors. We characterize fundamental monitoring limitations from system-theoretic and graph-theoretic perspectives. We design centralized and distributed attack detection and identification schemes. We provide insight into the design of coordinated attacks amenable to simple implementation, and we validate our findings through smart grid applications [external page 1] and [external page 2].